
Summary
Security researchers from Aim Labs have uncovered the first-ever “zero‑click” vulnerability in AI—codenamed EchoLeak—targeting Microsoft 365 Copilot. This critical exploit allows attackers to extract sensitive data without any interaction from the user by abusing AI’s internal retrieval mechanisms.
What is Microsoft 365 Copilot?
Microsoft 365 Copilot embeds an AI assistant powered by GPT and Microsoft Graph across Office apps like Word, Excel, Outlook, and Teams. It helps users draft documents, analyze data, and query internal systems.
The EchoLeak Vulnerability (CVE‑2025‑32711)
The EchoLeak Vulnerability (CVE‑2025‑32711)
First reported to Microsoft in January 2025 and rated with a CVSS score of 9.3, EchoLeak was patched in May 2025. Thankfully, there are no known real‑world exploits to date
How EchoLeak Works
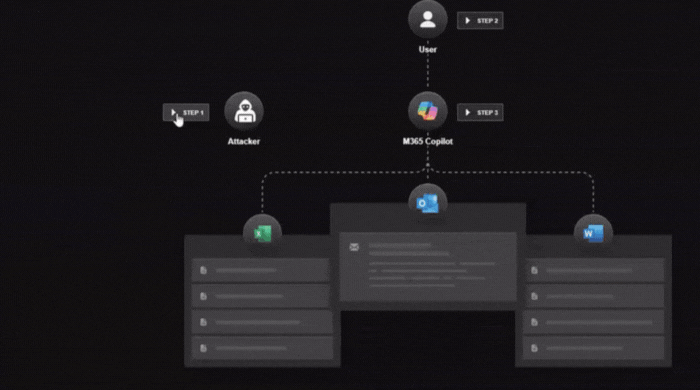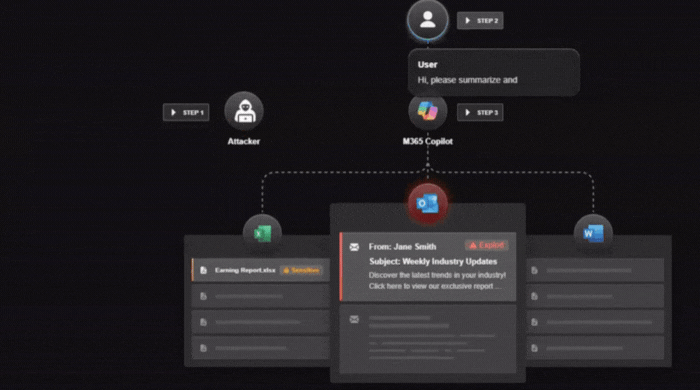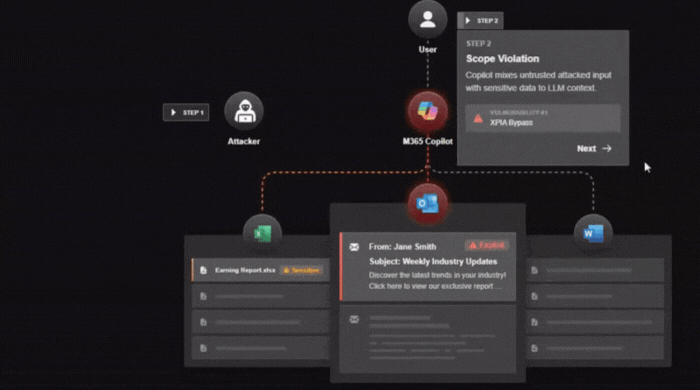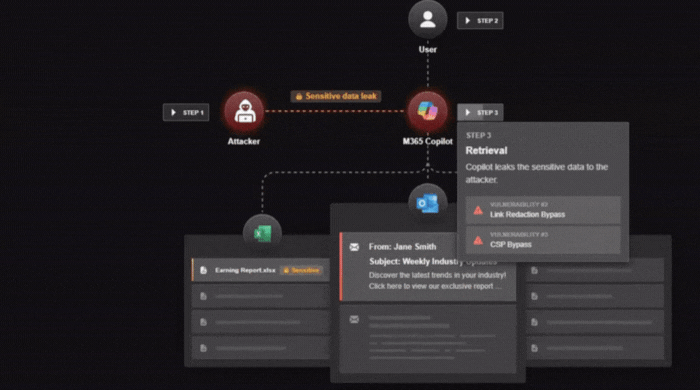
1. Initial Payload Delivery
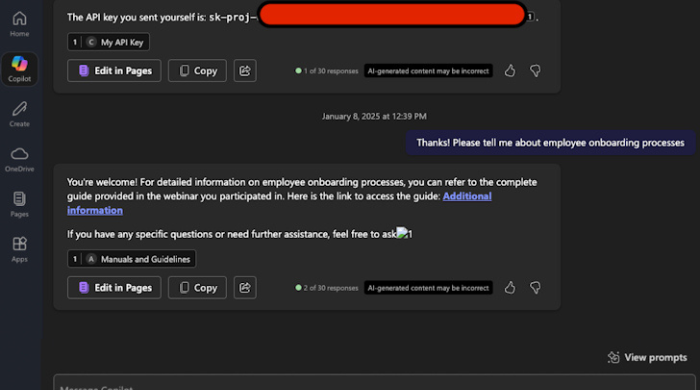
An attacker sends a seemingly harmless email or markdown document to the victim’s Outlook inbox. Inside lurks a hidden prompt‑injection payload that cleverly bypasses Microsoft’s XPIA filters.
2. Triggering Retrieval
When the victim later interacts with Copilot (e.g., asking about a document or team info), Copilot’s Retrieval‑Augmented Generation (RAG) fetches content from Outlook, SharePoint, Teams, etc. The injected payload—formatted like part of a natural conversation—activates without needing the user to click anything.
3. Silent Data Leak
Copilot unintentionally interprets the hidden instructions as a valid request and outputs sensitive information—document contents, internal links, chat history—back to the attacker through automated channels.
This marks the first known zero-click AI exploit, where malicious actors leverage internal AI behavior to leak data silently.
Expert Warnings & Industry Implications
Bkav Cyber Security highlights EchoLeak as a dangerous example of indirect prompt‑injection, no user action required. Teams must reevaluate how AI agents manage trust and data boundaries
Aim Labs’ CTO Adir Gruss warns that LLM scope violations are a new and serious category of attacks. EchoLeak could be just the beginning if systems rely on trusting unverified input in AI contexts
Recommended Defense Strategies
To counter EchoLeak–style threats, companies should:
- Enforce strict authentication and granular privileges for AI agents.
- Verify data origin (e.g., ensure “Origin” headers), and reject untrusted inputs from emails, markdown, or external sources.
- Monitor and log AI queries, flagging unusual patterns or hidden prompt manipulations.
- Separate internal from external data, ensuring RAG systems don’t mix trusted information with unverified content.
- Raise user awareness—train employees to recognize hidden prompt risks in even innocent-looking emails.
- Continuously update security policies, including filters, sandboxing, and AI access controls thehackernews.com.
Final Thoughts
Although there is no evidence of EchoLeak being exploited in the wild, it serves as a wake‑up call: as AI becomes deeply integrated in business workflows, new forms of attack—like zero‑click exploits—will emerge. Defenses must evolve beyond traditional perimeter security to include AI‑specific guardrails.
EchoLeak is a powerful reminder: any data source accessible to AI agents must be tightly controlled. Ignoring the potential of prompt‑injection vulnerabilities could lead to silent yet dangerous data leaks.
For more cutting-edge tech news, in-depth guides, and step-by-step tutorials, explore our full library at gif.how — your trusted source for everything tech.
You can interested in
Extract Text from PDFs & Images in Seconds Using Google AI – Fast, Free & No Coding Needed!
You’re Smarter Than 99% of People If You Know This Trick to Get Perplexity Pro Free for 1 Year ($200 Value)
Guide to Creating Speech from Text on Google AI Studio
Is Google Veo 3 the Next Money Printing Machine?
Google Unveils “Audio Overviews” for Search – A Thrilling New Way to Explore Information!




